How to Spot and Avoid Phishing Scams
The sections immediately below contain quick guides that you can use to protect yourself against phishing. Further down the page you can find detailed examples of email phishing and the tech support scam.
You can use the following behaviours to help you better evaluate if a message may be a phishing attempt:
- Think: Consider the request in detail. Is this normal or expected behaviour from this person?
- Pause: The message has an unusual sense of urgency, requiring your immediate attention.
- Identify: Check very carefully the sender’s name and email address. Does it look right?
- React: Be warned by spelling errors, bad grammar, odd formatting, or missing signatures.
- Links: The message asks you to log in or provide personal information to a website.
- Files: There is an attachment you were not expecting, like an invoice.
Examples of phishing techniques in messages appear later in this article.
If you suspect a message may be a phishing attempt, consider the following suggestions. They can help guide your next steps:
- Call the sender to verify. If there's any doubt at all, make a call.
- If you’re on a mobile device, wait until you’re on a computer so you can check more carefully.
- Do not reply on act on unusual or out of character emails. Question urgency.
- Do not open email attachments or click links in suspicious e-mails. Hover the mouse over the link to reveal the real destination address.
- Ensure the login page is truly what it says it claims to be. Check the URL carefully! Make sure it is a login page you’ve used before. It should be grammatically correct and professional.
Please report a phishing scam or spam email by forwarding the message as an attachment to spam@uwindsor.ca or contact the Service Desk at ext. 4440.
Watch this video on how to avoid taking the bait.
The United Kingdom’s Centre for the Protection of National Infrastructure has produced a quiz to test your skill at spotting phishing attempts (PDF format).
Detecting Signs of Email Phishing
1. Examine the email addresses
The email addresses on an email message can reveal that a message is not legitimate. A careful examination can keep you safe.
There are three important areas to look at in the email addresses of a message:
- From: friendly name
- From: email address
- Reply-to: address
WARNING SIGN: MISLEADING FRIENDLY NAMES
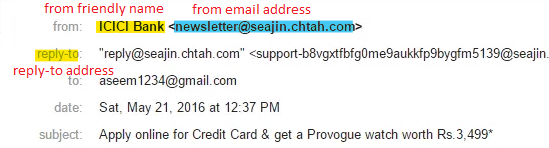
The From: friendly name is a feature designed to provide an easy-to-read identifier for the sender of the message instead of a potentially cryptic email address. For instance, a friendly name might be “John Testerski – IT Services” instead of the less informative jtester@uwindsor.ca email address.
The From: friendly name feature, however, can be abused because many email clients only display the friendly name rather than the actual From: email address, which is the address where a reply would be sent. This allows phishers to use misleading friendly names.
The example above highlights a misleading From: friendly name. The From: friendly name is “ICICI Bank” but the From: email address is “newsletter@seajin.chtah.com” which is clearly not ICICI Bank.
Safety Tip: Check the From: email address in addition to the From: friendly name. This can be hard to do on mobile devices, so if you’re in doubt, examine the message again from a desktop or laptop computer.
WARNING SIGN: MISDIRECTED REPLY-TO ADDRESS
Attackers will sometimes abuse the Reply-to: address to have replies to their messages go to a different address than what is in the From: email address. They will use a legitimate and correct address in the From: email address and will put their (the attacker’s) own email address in the Reply-to: address.

You can see in the sample message above that the attacker included a Reply-to: address that redirects replies to their own address @gmail.com instead of @uwindsor.ca.
Safety Tip: Examine the message for the presence of a Reply-to: address and examine it carefully to see if it is an attempt to misdirect your response. If in doubt on a mobile device, examine the message again from a desktop or laptop computer.
WARNING SIGN: LOOKALIKE CHARACTER CHANGES
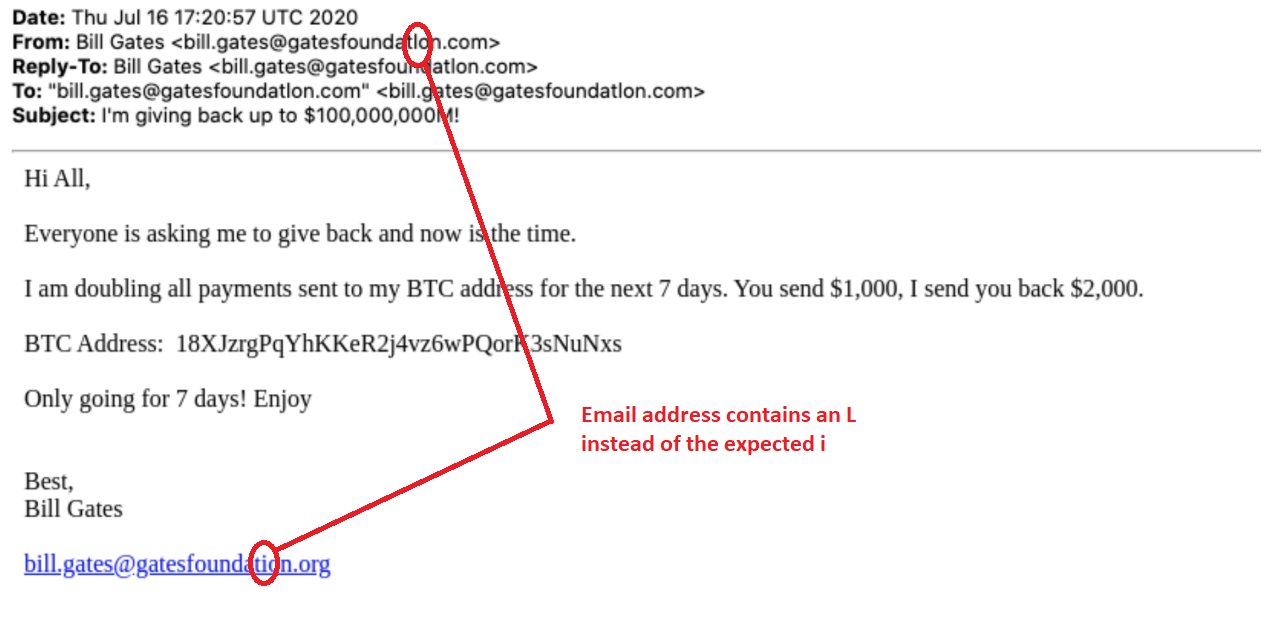 (taken from https://finance.yahoo.com/news/bill-gates-phishing-campaign-nearly-identical-to-twitter-takeover-211102156.html)
(taken from https://finance.yahoo.com/news/bill-gates-phishing-campaign-nearly-identical-to-twitter-takeover-211102156.html)Another threat technique phishers use in email and website addresses is lookalike character changes.
Several characters can easily be confused for one another. For instance, an uppercase i (‘I’) is difficult to distinguish from a lowercase L (‘l’), as in the example above. An attacker will sometimes very subtly change characters in an email address or web link so that at a quick glance it looks correct. A response to the manipulated email address, however, would go to the attacker’s mailbox instead of where the user expected.
Safety Tip: Always examine email addresses and web site addresses carefully to be sure that they are spelled the way they should be and go to the right address.
2. Recognize Common Content Clues
Phishing attempts can sometimes be detected because the message is somehow not normal. Some common warning signs of phishing messages are:
- Urgency
- Unusual request
- Strange phrasing
WARNING SIGN: URGENCY
Safety Tip: When a message arrives asking for urgent action, take the time to consider and verify it anyway. Call or text the individual on their phone (don’t use email).
WARNING SIGN: UNUSUAL REQUESTS
A message that arrives unexpectedly asking you to do something unusual or sounds like it is out of character for the person sending the message is a warning sign that someone may be phishing. These requests often ask for a favour by someone who is supposedly too busy to do it themselves.
Safety Tip: If something feels strange or odd, validate the message’s authenticity before acting. Call or text the individual on their phone (don’t use email).
WARNING SIGN: STRANGE PHRASING
Everyone has their own writing style. If a message arrives from someone and does not look like their messages (lack of signature, different structure, etc.) or uses words and phrasing that the person does not commonly use, it is possibly a fake.
Safety Tip: Examine the message carefully for other signs that it may not be legitimate, such as a different format or structure than you expect. Call or text the individual on their phone (don’t use email).
Example:
Below is an example of a Gift Card Scam phishing message that uses both urgency and contains an unusual request. The sender is busy (“in a meeting”) and needs something urgently (“help with that right now”). It also uses phrasing (“putting this to you”) that may not be something the supposed sender (Sally Jones) uses regularly.
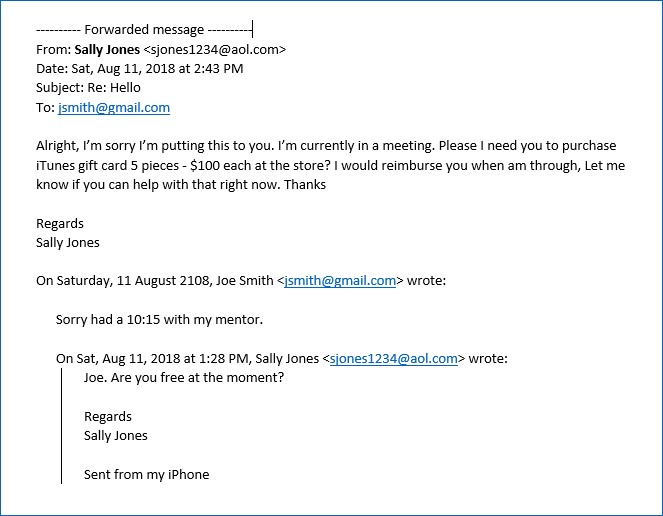
(taken from https://www.apa.org/about/division/officers/dialogue/2018/01/email-scams.aspx)
3. Link text and link destination
Paying attention to the links in a message and noting where they actually go is important.
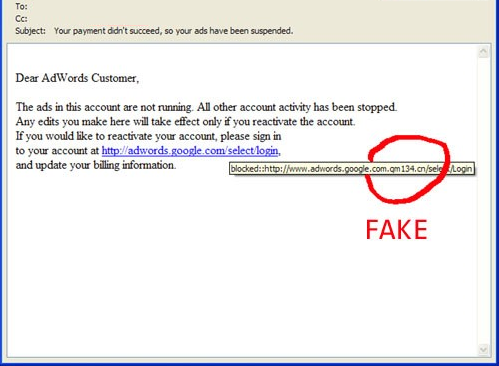
(modified from https://www.reinhartmarketing.com/news/how-to-detect-scam-emails/)
When people include web page links in messages, they are composed of two elements:
- Link text
- Link destination
The link text is what is displayed on the screen to the user. The link destination is the web site that the web browser will open. These two elements do not have to be the same. As in the example above, this can be abused by an attacker to make you think the web link goes to one web site based on the link text, but the link destination goes somewhere completely different.
Safety Tip: Hover your mouse over the link text. The link destination will appear, either under your mouse pointer or in the status area at the bottom of the window. You cannot hover over links on a mobile device. Do not click links in messages on your mobile device. Wait until you are back at your computer and can use the hover technique to determine the link destination.
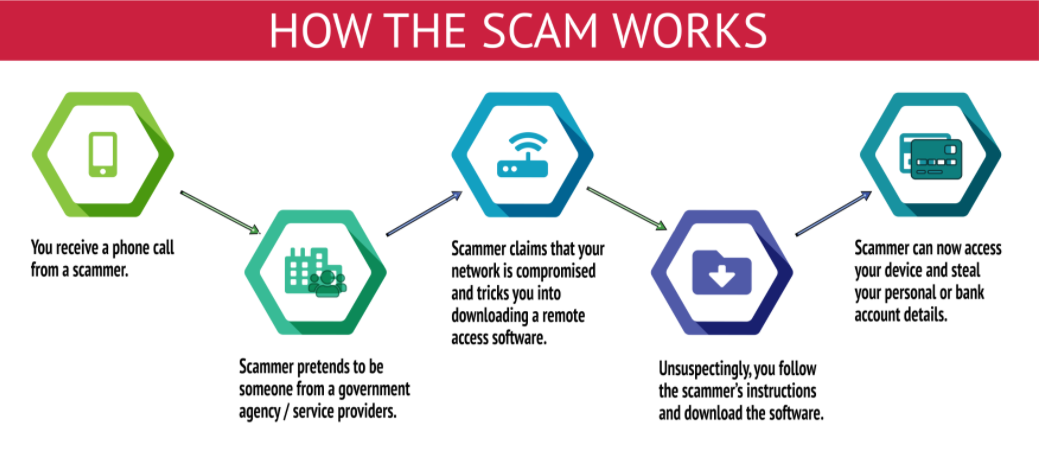
Detecting a Tech Support Phishing Scam
1. Unsolicited telephone call or message.
Someone will contact you unexpectedly, usually by telephone or voicemail.
WARNING SIGNS: The voice may be a recording, the message does not mention your name, or you have to press a button to get to a person.
The attacker will claim to be from some recognizable company, such as a bank or financial institution, Amazon, Netflix, or an Internet Service Provider.
The name of the company will be recognizable so even though you do not have a Netflix account, you recognize the name and begin to get concerned.
Safety Tip: Wait for them to call back. If it is truly important, the company will call again.
(source: https://www.csa.gov.sg/singcert/resources/infographics/tech-support-scam)
2. An urgent issue.
There will be some unexpected, time-sensitive problem that they are calling you about.
WARNING SIGN: The person cannot provide specific details about the problem.
They will explain that there is something wrong, like unusual charges on your account or a subscription that is about to expire or a problem with your computer. They’ll speak generically, without much detail.
Things to check:
- Do you even have an account with or use a computer from that company?
- If you have setup transaction alerts with your financial institution, have you received a message that confirms what the person is claiming?
- Ask for specific details about the issue – names, account numbers, dates and times.
Safety Tip: Double-check the accounts yourself. Log on using a different computer or call the company using a number you look up yourself.
3. Request for remote access
The attacker will tell you the problem cannot be solved over the phone and that a screen share is necessary.
WARNING SIGN: Attacker wants you to download software giving them remote access.
The attacker wants to get access to your computer. They will offer to help solve the problem via a remote support screen sharing or remote access session. They will use this access to gain access to your accounts or to install malware of ransomware on your computer.
Safety Tip: Never allow remote access to someone who called you.
(source: https://www.csa.gov.sg/singcert/resources/infographics/tech-support-scam)
We're here to help!
IT Services is happy to answer questions about cybersecurity on campus: ext. 4440 or open a ticket for service here: uwindsor.ca/itshelp. More information on cybersecurity issues facing campus: uwindsor.ca/cybersecurity